WHY INFORMATION SYSTEMS ARE IMPORTANT
An understanding of the effective and responsible use and management of information systems is important for managers and other business knowledge workers in today’s global information society. Information systems and technologies have become a vital component of successful businesses and organizations. Information systems constitute an essential field of study in business administration and management, as they are considered a major functional area in business operations.
WHAT YOU NEED TO KNOW
Managerial end users need to know how information systems can be employed successfully in a business environment. The important question for any business end user or manager is: What do you need to know in order to help manage the hardware, software, data, and network resources of your business, so they are used for the strategic success of your company?
An IS Framework for Business Professionals:
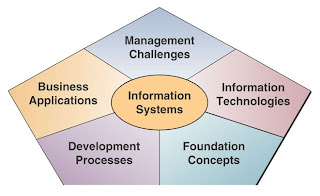
Managers or business professionals are not required to know the complex technologies, abstract behavioral concepts, or the specialized applications involved in the field of information systems. Figure below illustrates a useful conceptual framework that outlines what a manager or business professional needs to know about information systems. It emphasizes five areas of knowledge:
• Foundation Concepts
• Information Technologies
• Business Applications
• Development Processes
• Management Challenges
What is an Information System?
An information system (IS) can be any organized combination of people, hardware, software, communications networks, and data resources that collect, transforms, and disseminate information in an organization.
 Information Technologies:
Information Technologies: Business professionals rely on many types of information systems that use a variety of information technologies. For example:
Types of IS - Manual (paper-and-pencil) information systems
- Informal (word-of-mouth) information systems
- Formal (written procedures) information systems
- Computer-based information systems
Computer-based information systems (IS) use hardware, software, the Internet, and other telecommunications networks, computer-based data resource management techniques, and other forms of information technologies (IT) to transform data resources into a variety of information products for consumers and business professionals.
SYSTEM CONCEPTS
System concepts underlie the field of information systems. Understanding system concepts will help you understand many other concepts in the technology, applications, development, and management of information systems. System concepts help you understand:
• Technology. That computer networks are systems of information processing components that uses a variety of hardware, software, data and telecommunication technologies.
• Applications. That electronic business and commerce involves interconnected business information systems.
• Development. That developing ways to use information technology n business includes designing the basic components of information systems.
• Management. That managing information technology emphasizes the quality, strategic business value, and security of an organization’s information systems.
What is a System?
Question: What is a system as it applies to the concept of an information system?
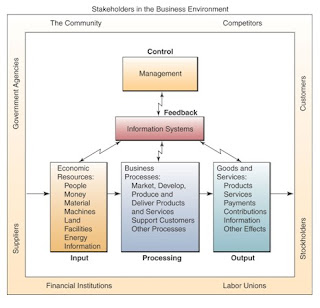
Answer: A system is a group of interrelated components working together toward a common goal by accepting inputs and producing outputs in an organized transformation process.
A system (sometimes called a dynamic system) has three basic interacting components or functions. These include:
• Input involves capturing and assembling elements that enter the system to be processed.
• Processing involves transformation processes that convert input into output.
• Output involves transferring elements that have been produced by a transformation process to their ultimate destination.
Feedback and Control:
Two additional components of the system concept include feedback and control. A system with feedback and control components is sometimes called a cybernetic system, that is, a self-monitoring, self-regulating system.
• Feedback is data about the performance of a system.
• Control involves monitoring and evaluating feedback to determine whether a system is moving toward the achievement of its goals. The control function then makes necessary adjustments to a system's input and processing components to ensure that it produces proper output.
Other System Characteristics:
A system does not exist in a vacuum; rather, it exists and functions in an environment containing other systems.
Subsystem: A system that is a component of a larger system, where the larger system is its environment.
System Boundary: A system is separated from its environment and other systems by its system boundary.
Interface: Several systems may share the same environment. Some of these systems may be connected to one another by means of a shared boundary, or interface.
Open System: A system that interacts with other systems in its environment is called an open system (connected to its environment by exchanges of inputs and outputs).
Adaptive System: A system that has the ability to change itself or its environment in order to survive is called an adaptive system.
COMPONENTS OF AN INFORMATION SYSTEM
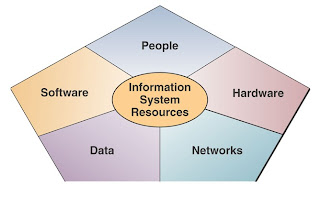
An information system model expresses a fundamental conceptual framework for the major components and activities of information systems. An information system depends on the resources of people, hardware, software, data, and networks to perform input, processing, output, storage, and control activities that convert data resources into information products.
The information systems model outlined in the text emphasizes four major concepts that can be applied to all types of information systems:
• People, hardware, software, data, and networks, are the five basic resources of information systems.
• People resources include end users and IS specialists, hardware resources consist of machines and media, software resources include both programs and procedures, data resources can include data and knowledge bases, and network resources include communications media and networks.
• Data resources are transformed by information processing activities into a variety of information products for end users.
• Information processing consists of input, processing, output, storage, and control activities.
 INFORMATION SYSTEM RESOURCES
INFORMATION SYSTEM RESOURCES The basic IS model shows that an information system consists of five major resources:
• People resources
• Hardware resources
• Software resources
• Data resources
• Network resources
People Resources:
People are required for the operation of all information systems. These people resources include end users and IS specialists.
• End Users (also called users or clients) are people who use an information system or the information it produces. Most of us are information system end users. And most end users in business are knowledge workers, that is, people who spend most of their time communicating and collaborating in teams of workgroups and creating, using, and distributing information.
• IS Specialists are people who develop and operate information systems. They include system analysts, software developers, system operators, and other managerial, technical, and clerical IS personnel.
Systems analysts – design information systems based on the information requirements of end users.
Software developers – create computer programs based on the specifications of systems analysts.
System operators – monitor and operate large computer systems and networks.
Hardware Resources:
Hardware resources include all physical devices and materials used in information processing.
• Machines - physical devices (computers, peripherals, telecommunications networks, etc.)
• Media - all tangible objects on which data are recorded (paper, magnetic disks etc.)
Examples of hardware in computer-based information systems are:
• Computer Systems – which consist of central processing units containing microprocessors, and a variety of interconnected peripheral devices.
• Computer peripherals – which are devices such as a keyboard or electronic mouse for input of data and commands, a video screen or printer for output of information, and magnetic or optical disks for storage of data resources.
Software Resources:
Software resources include all sets of information processing instructions.
• Program - a set of instructions that causes a computer to perform a particular task.
• Procedures - set of instructions used by people to complete a task.
Examples of software resources are:
• System software – such as an operating system program, that controls and supports the operations of a computer system.
• Application software – are programs that direct processing for a particular use of computers by end users.
• Procedures – are operating instructions for the people who will use an information system.
Data Resources:
Data constitutes a valuable organizational resource. Thus, data resources must be managed effectively to benefit all end users in an organization. The data resources of information systems are typically organized into:
• Databases - a collection of logically related records or files. A database consolidates many records previously stored in separate files so that a common pool of data records serves many applications.
• Knowledge Bases - which hold knowledge in a variety of forms such as facts and rules of inference about various subjects.
Data versus Information. The word data is the plural of datum, though data is commonly used to represent both singular and plural forms. The term’s data and information are often used interchangeably. However, you should make the following distinction:
Data: - are raw facts or observations, typically about physical phenomena or business transactions. More specifically, data are objective measurements of the attributes (characteristics) of entities, such as people, places, things, and events.
Information: - is processed data, which has been placed in a meaningful and useful context for an end user. Data is subjected to a “value-added” process (data processing or information processing) where:
• Its form is aggregated, manipulated, and organized.
• Its content is analyzed and evaluated
• It is placed in a proper context for a human user
Network Resources:
Telecommunications networks like the Internet, intranets, and extranets have become essential to the successful electronic business and commerce operations of all types of organizations and their computer-based information systems. Telecommunications networks consist of computers, communications processors, and other devices interconnected by communications media and controlled by communications software. The concept of network resources emphasizes that communications networks are a fundamental resource component of all information systems. Network resources include:
• Communications media (twisted-pair wire, coaxial cable, fiber-optic cable, and microwave, cellular, and satellite wireless systems.
• Network support (people, hardware, software, and data resources that directly support the operation and use of a communications network).
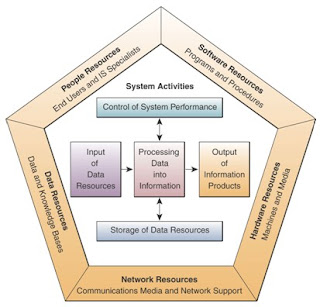
INFORMATION SYSTEM ACTIVITIES
Information processing (or data processing) activities that occur in information system include the following:
• Input of data resources
• Processing of data into information
• Output of information products
• Storage of data resources
• Control of system performance
Input of Data Resources:
• Data about business transactions and other events must be captured and prepared for processing by the input activity. Input typically takes the form of data entry activities such as recording and editing.
• Once entered, data may be transferred onto a machine-readable medium such as magnetic disk or type, until needed for processing.
Processing of Data into Information:
• Data is typically subjected to processing activities such as calculating, comparing, sorting, classifying, and summarizing. These activities organize, analyze, and manipulate data, thus converting them into information for end users.
• A continual process of correcting and updating activities must maintain quality of data stored in an information system.
Output of Information Products:
• Information in various forms is transmitted to end-users and made available to them in the output activity. The goal of information systems is the production of appropriate information products for end users.
Storage of Data Resources:
Storage is a basic system component of information systems.
• Storage is the information system activity in which data and information are retained in an organized manner for later use.
Control of System Performance:
An important information system activity is the control of its performance.
• An information system should produce feedback about its input, processing, output, and storage activities.
• Feedback must be monitored and evaluated to determine if the system is meeting established performance standards.
• Feedback is used to make adjustments to system activities to correct deficiencies.
RECOGNIZING INFORMATION SYSTEMS
As a business professional, you should be able to recognize the fundamental components of information systems you encounter in the real world. This means that you should be able to identify:
• The people, hardware, software, data, and network resources they use.
• The types of information products they produce.
• The way they perform input, processing, output, storage, and control activities.
Analysing BellSouth’s Information System
From the Real World Case of BellSouth Corporation, we will try to recognize or visualize the resources used, activities performed, and information products produced by their information systems.
IS Resources:
• People resources include end users like BellSouth’s online customers and employees, and IS specialists like CIO Fran Dramis and project leader Lori Groves.
Hardware Resources:
• Thousands of PC server
• Other computers that BellSouth and its customers must be using
Software Resources:
• Web browsers
• Operating systems
• e-commerce websites software
• Oracle’s customer relationship management system
• Other proprietary BellSouth business software.
Network Resources:
• Communications media and network support components that are part of the network resources that BellSouth would need to support the e-business and e-commerce activities of such a large telecommunications company.
Data Resources:
• Computer-accessible databases of data about their customers, employees, services, and other necessary business information.
Information Products:
• Displays on customer and employee networked PCs that provide information about and support the provision of BellSouth’s services, such as you would find by visiting their Websites at www.bellsouth.com and www.bellsouthcorp.com.
IS Activities:
• Input activities include the input of Web site navigation clicks and e-commerce and e-business data entries and selections, and online collaboration queries and responses made by customers, suppliers, and employees.
Processing Activities:
• Processing activities are accomplished whenever any of BellSouth’s computers executes the programs that are part of their e-business and e-commerce software resources.
Output Activities:
• Output activities primarily involve the display or printing of information products mentioned earlier.
Storage Activities:
• Storage activities take place whenever business data is stored and managed in the files and databases on the disk drives and other storage media of BellSouth’s computer systems.
Control Activities:
• Control activities include the use of passwords and other security codes by customers, suppliers, and employees for entry into BellSouth’s e-business and e-commerce websites, and access of their databases and knowledge bases.
Section II: Foundation Concepts: Business Applications, Development, and Management
THE FUNDAMENTAL ROLES OF IS APPLICATIONS IN BUSINESS
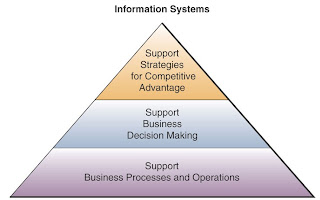
Information systems perform three vital roles in any type of organization. That is, they support an organization’s:
• Business processes and operations
• Decision making by employees and managers
• Strategies for competitive advantage
The Major Roles of IS: Examples
Three major roles of the business applications of information systems include:
• Support Business Processes – involves dealing with information systems that support the business processes and operations in a business.
• Support Decision Making – help decision makers to make better decisions and attempt to gain a competitive advantage.
• Support Competitive Advantage – help decision makers to gain a strategic advantage over competitors requires innovative use of information technology.
e-BUSINESS IN BUSINESS
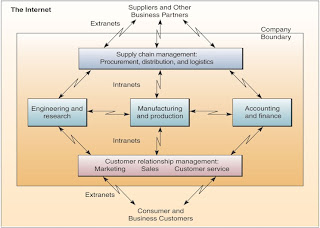
The explosive growth of the Internet and related technologies and applications is revolutionizing the way businesses are operated and people work, and how information technology supports business operations and end user work activities.
e-business is defined as the use of Internet technologies to internetwork and empower business processes, electronic commerce, and enterprise communication and collaboration within a company and with its customers, suppliers, and other business stakeholders.
Enterprise collaboration systems involve the use of groupware tools to support communication, coordination, and collaboration among the members of networked teams and workgroups. An internetworked e-business enterprise depends on intranets, the Internet, extranets, and other networks to implement such systems.
Electronic commerce is the buying and selling, and marketing and servicing of products, services, and information over a variety of computer networks. An internetworked e-business enterprise uses the Internet, intranets, extranets, and other networks to support every step of the commercial process.
TRENDS IN INFORMATION SYSTEMS
The roles given to the information systems function have expanded significantly over the years.
1950s - 1960s - Data Processing - Electronic data processing systems
Role: Transaction processing, record keeping, and accounting, and other electronic data processing (EDP) applications
1960s - 1970s - Management Reporting – Management information systems
Role: Providing managerial end users with predefined management reports that would give managers the information they needed for decision-making purposes.
1970s - 1980s - Decision Support - Decision support systems
Role: The new role for information systems was to provide managerial end users with ad hoc support of their decision-making process. This support would be tailored to the unique decision-making styles of managers as they confronted specific types of problems in the real world.
1980s - 1990s - Strategic and End User Support
Role: End users could use their own computing resources to support their job requirements instead of waiting for the indirect support of corporate information services departments.
• End User Computing Systems
Role: Direct computing support for end user productivity and work group collaboration.
• Executive Information Systems (EIS) -
Role: These information systems attempt to give top executives an easy way to get the critical information they want, when they want it, tailored to the formats they prefer.
• Expert Systems (ES) and other Knowledge-Based Systems
Role: Expert systems can serve as consultants to users by providing expert advice in limited subject areas.
• Strategic Information Systems (SIS)
Role: Information technology becomes an integral component of business processes, products, and services that help a company gain a competitive advantage in the global marketplace.
1990s - 2000 – Electronic business and commerce systems
Role: The rapid growth of the Internet, intranets, extranets, and other interconnected global networks has revolutionising the operations and management of today’s business enterprises.